How Permission Assist Helps Ensure Data Accuracy
The users of Permission Assist have been (and always will be) better at knowing their data; however, as your partner, we work to exceed industry standards in providing tools and features that help you detect anomalies when they occur. Some examples of situations that might lead to anomalies include the following:
-
New version upgrades of the third-party application
-
Enhancements to application importers that include additional permissions
-
Previously unseen (but valid) permission values emitted
-
Permission/user discrepancies between SaaS and on-property installations of third-party applications
Permission Assist continues to add new user experiences related to application permission monitoring and validation so that when these anomalies occur, Permission Assist can help you quickly identify these types of situations. Some of the features you can use to help ensure your data is accurate are listed below:
These features along with our combined efforts throughout the process, you'll have the opportunity to review permissions and ensure integrity every step of the way.
Application Permission Imports
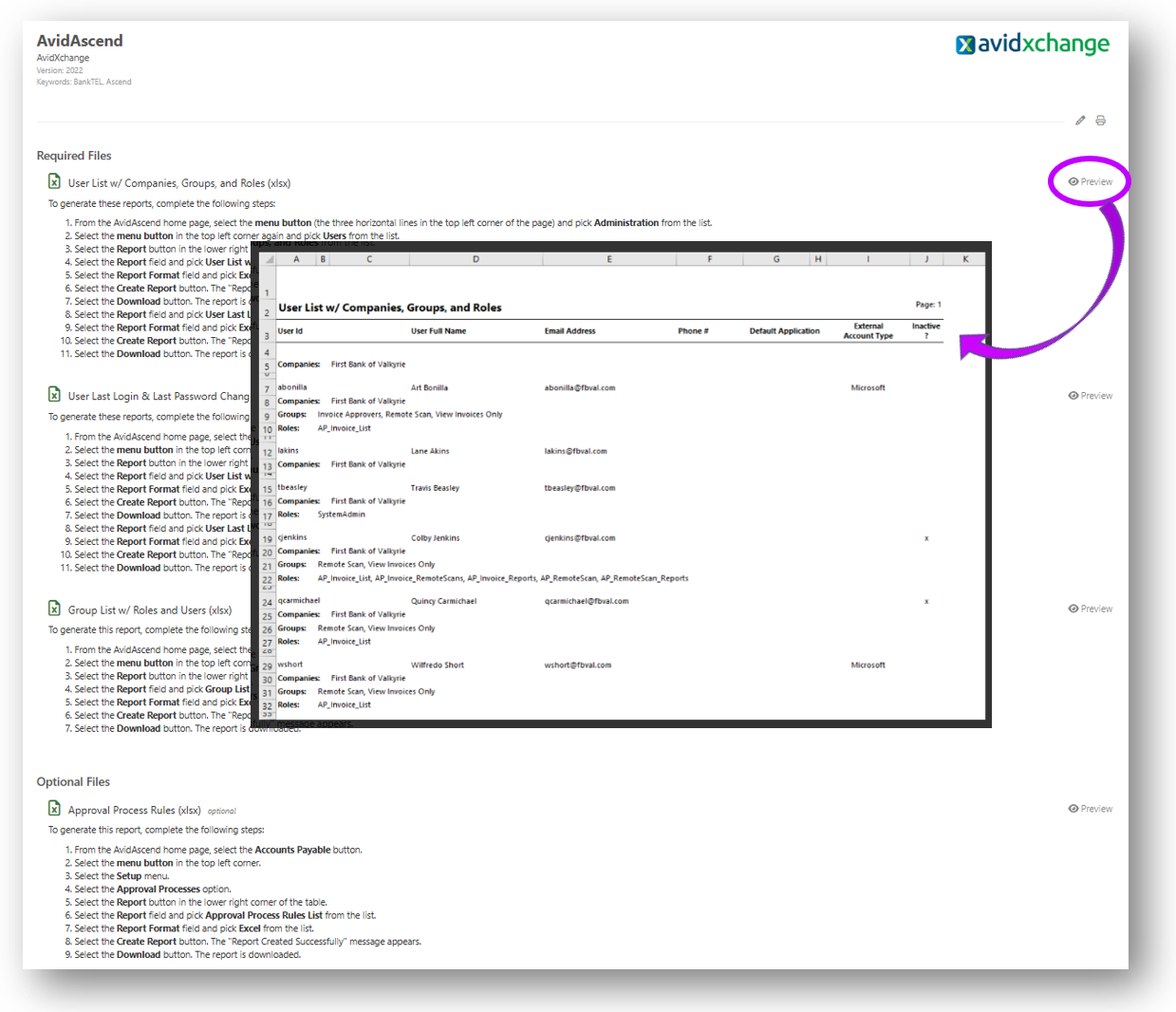
When importing permissions, some plugins require files and some will not. When files are required, the plugin includes built-in checks to ensure the correct files are imported. To provide clarity around which files are required and what format the files need to be in, the Settings tab within the application includes detailed documentation. Detailed instructions on how to generate the report in the proper format and an option to preview the file are also provided on the Settings tab whenever possible (see example below).
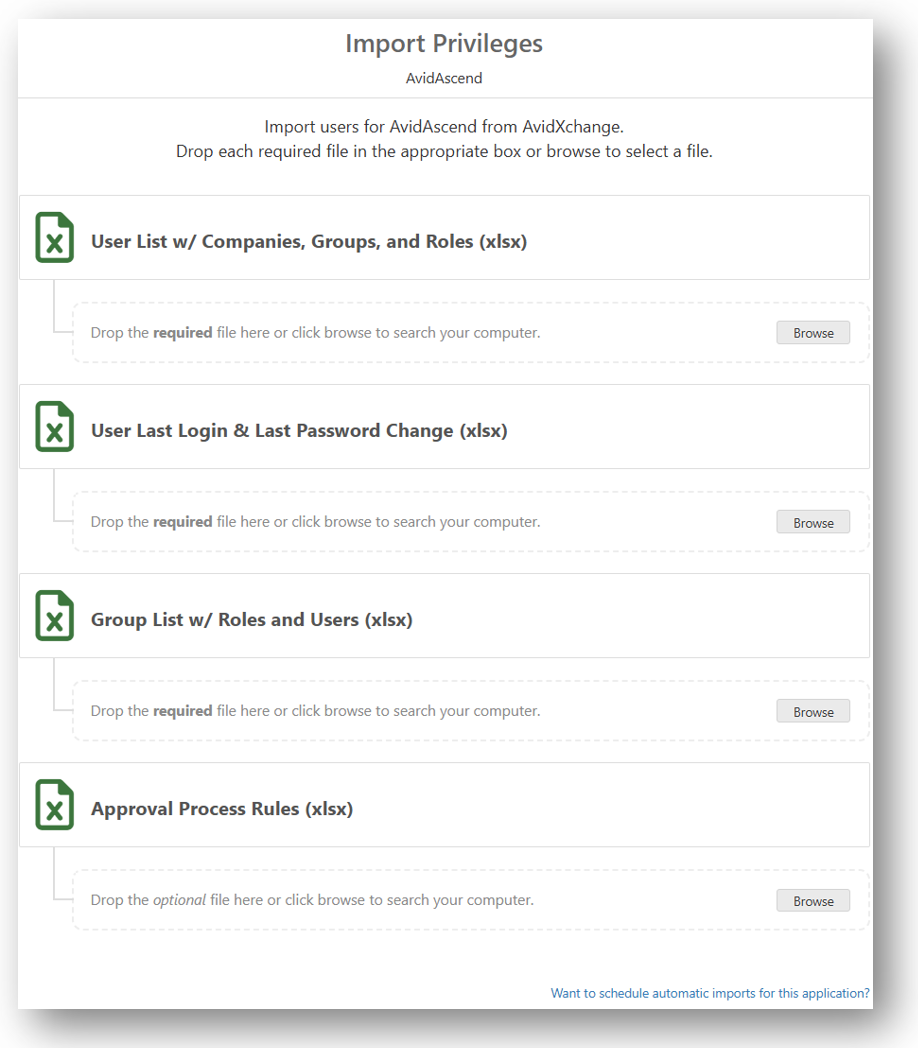
When importing data manually (meaning automatic imports aren't set up), you can easily see each file and the required file format as shown in the following example:
When the application allows for an API or similar direct connection to the security data, instructions and advanced configuration settings are used to ensure the configuration is correct and the appropriate data is scheduled for import (see example below).
Application Import and Change Logs
Import Log and Import Summary
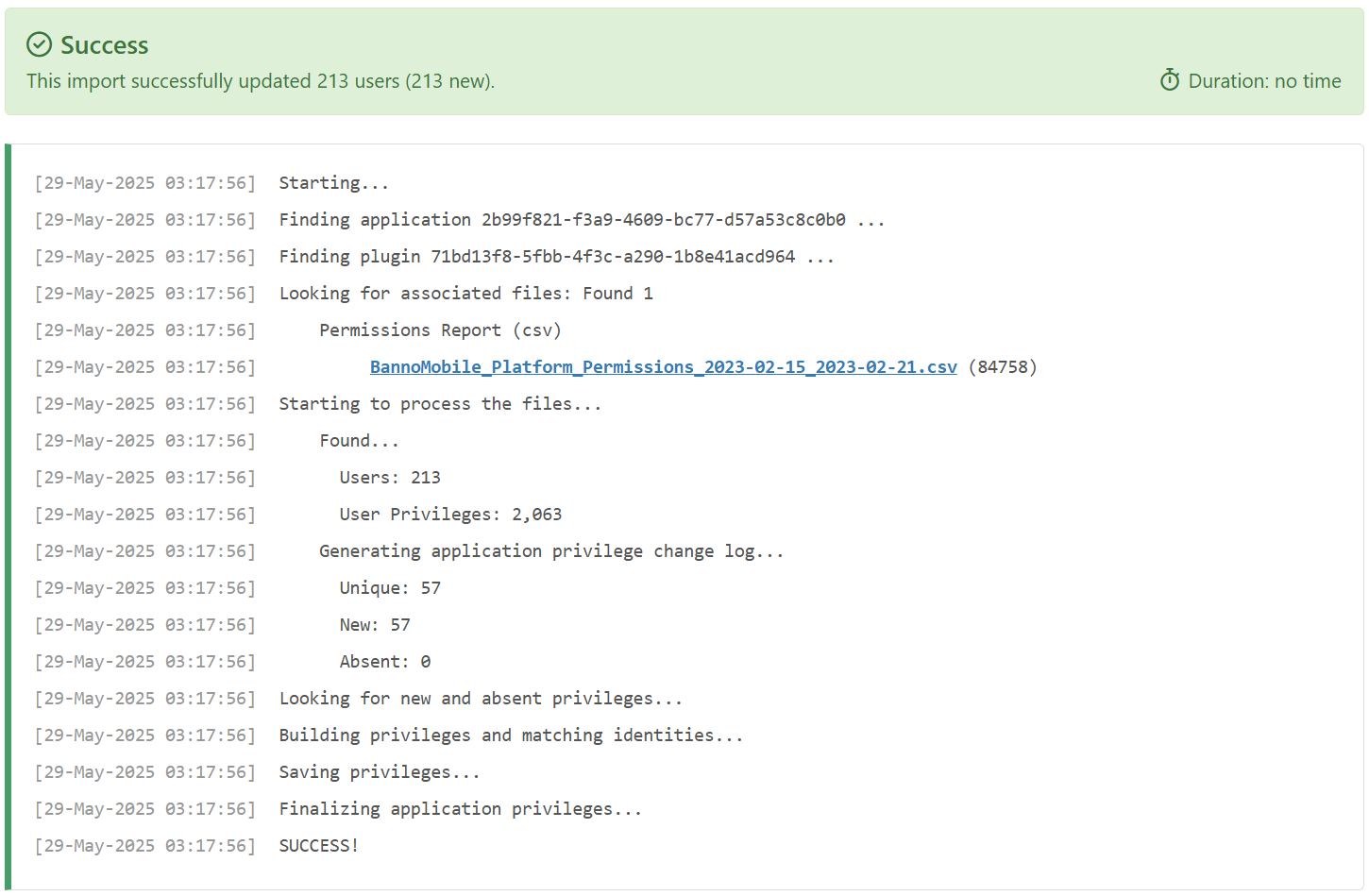
The Import Log within Permission Assist provides early progress and metrics through real-time display of progress as application permissions are being uploaded (see example below).
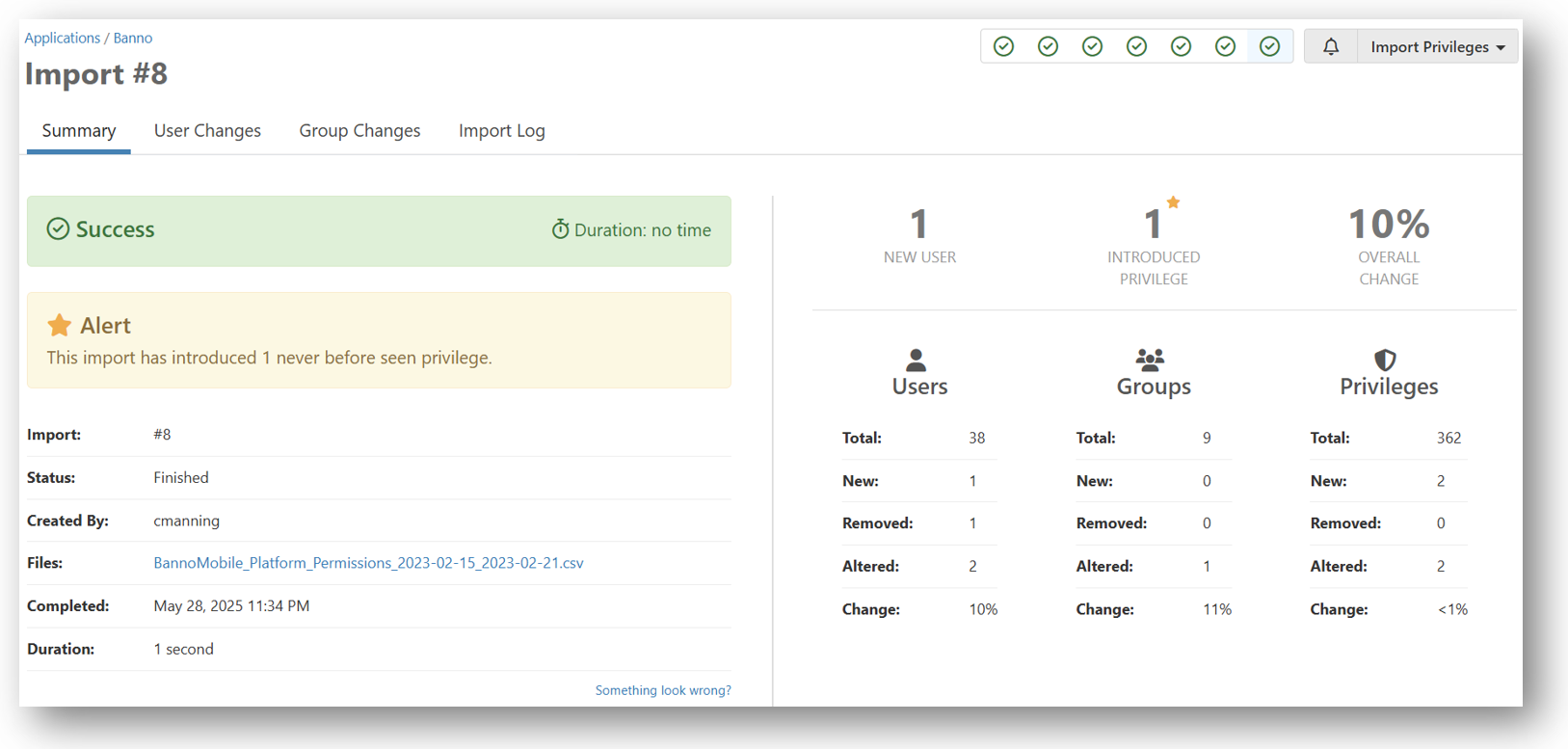
After the data is imported, a summary of new users and privileges is displayed (see example below).
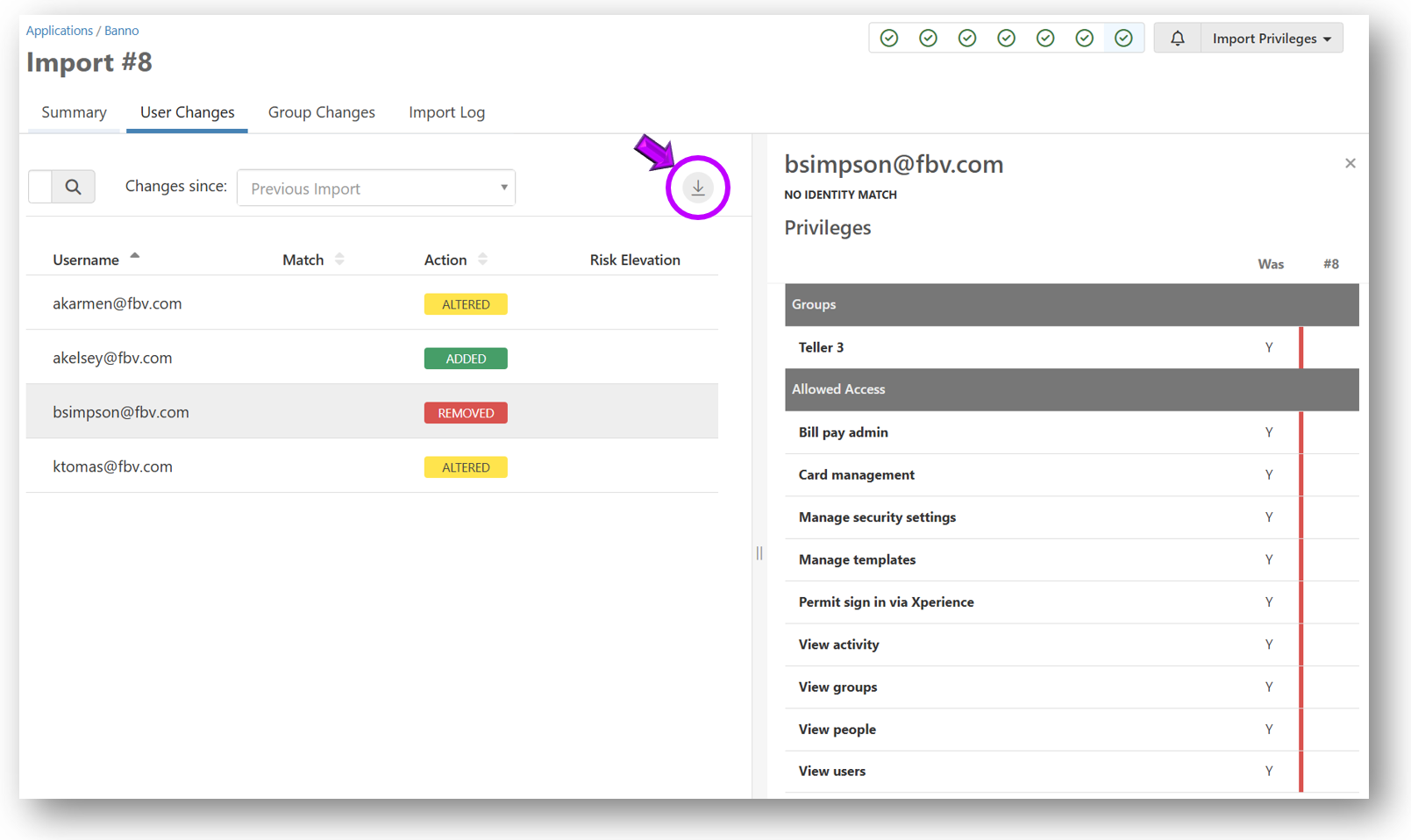
User Changes Log
The User Changes tab displays a list of all users that have been added or changed since the last import. If risk levels have been assigned to privileges within the application, Permission Assist is able to identify the potential risk those changes within the Risk Elevation column.
A more detailed view of the user's privileges as compared to a previous import is also available by selecting on a user within the list, and detailed reports of the changes.
Detailed reports of the changes are available in Excel or PDF format using the Export button (see below).
Sample Reports
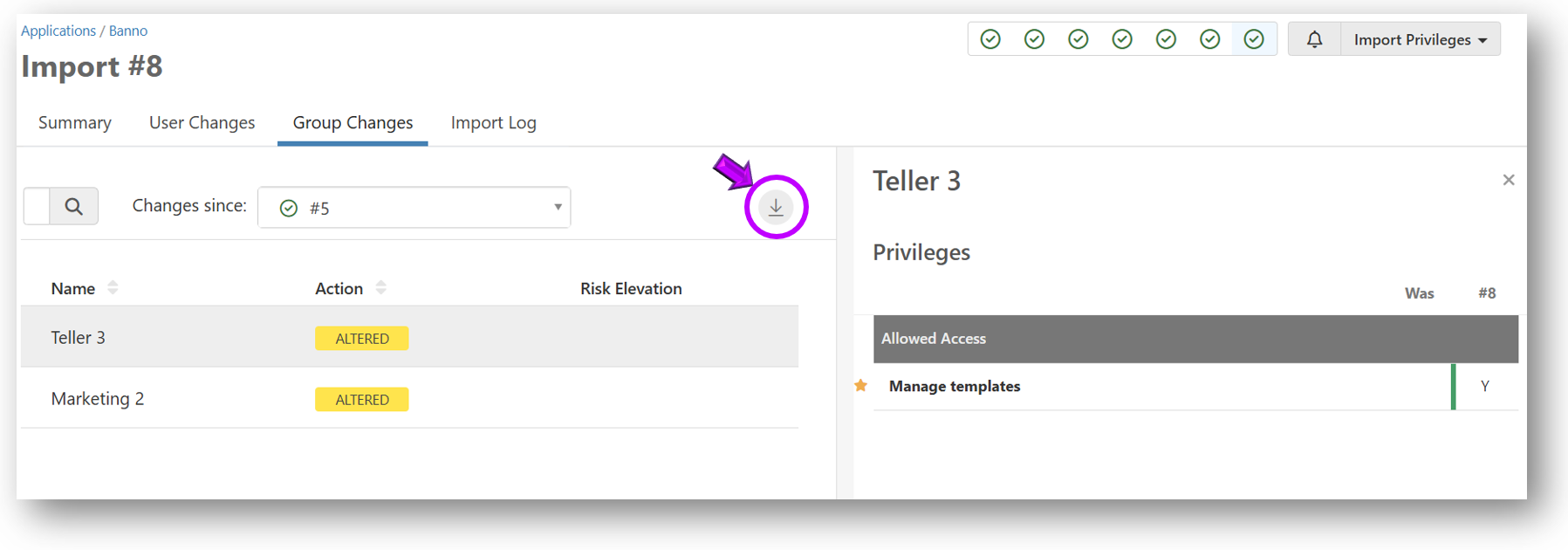
Group Changes Log
The User Changes tab displays a list of all groups that have been added or changed since the last import.
Detailed reports of the changes are available in Excel or PDF format using the Export button (see below).
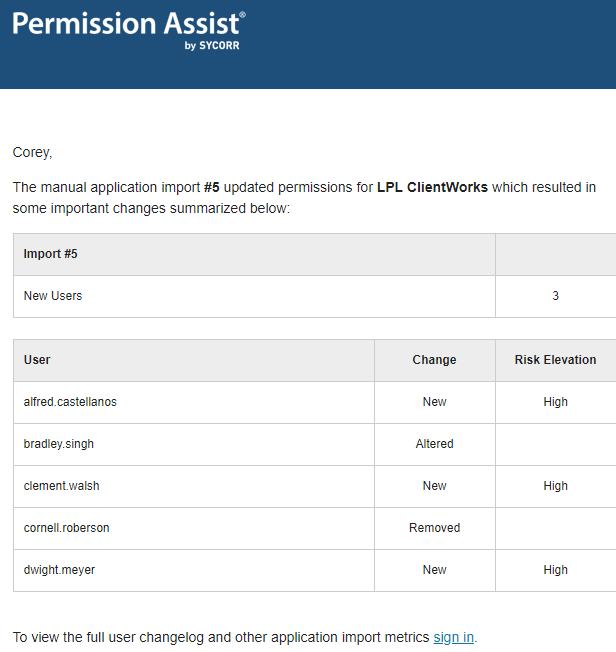
Application Alerts
Each user has the option of signing up for application alerts. When alerts are enabled for a specific application, Permission Assist sends an automatic email notification when user permissions for that application change. Within the email notification, a list of changes to permissions are highlighted along with the potential risk elevation associated with each change.
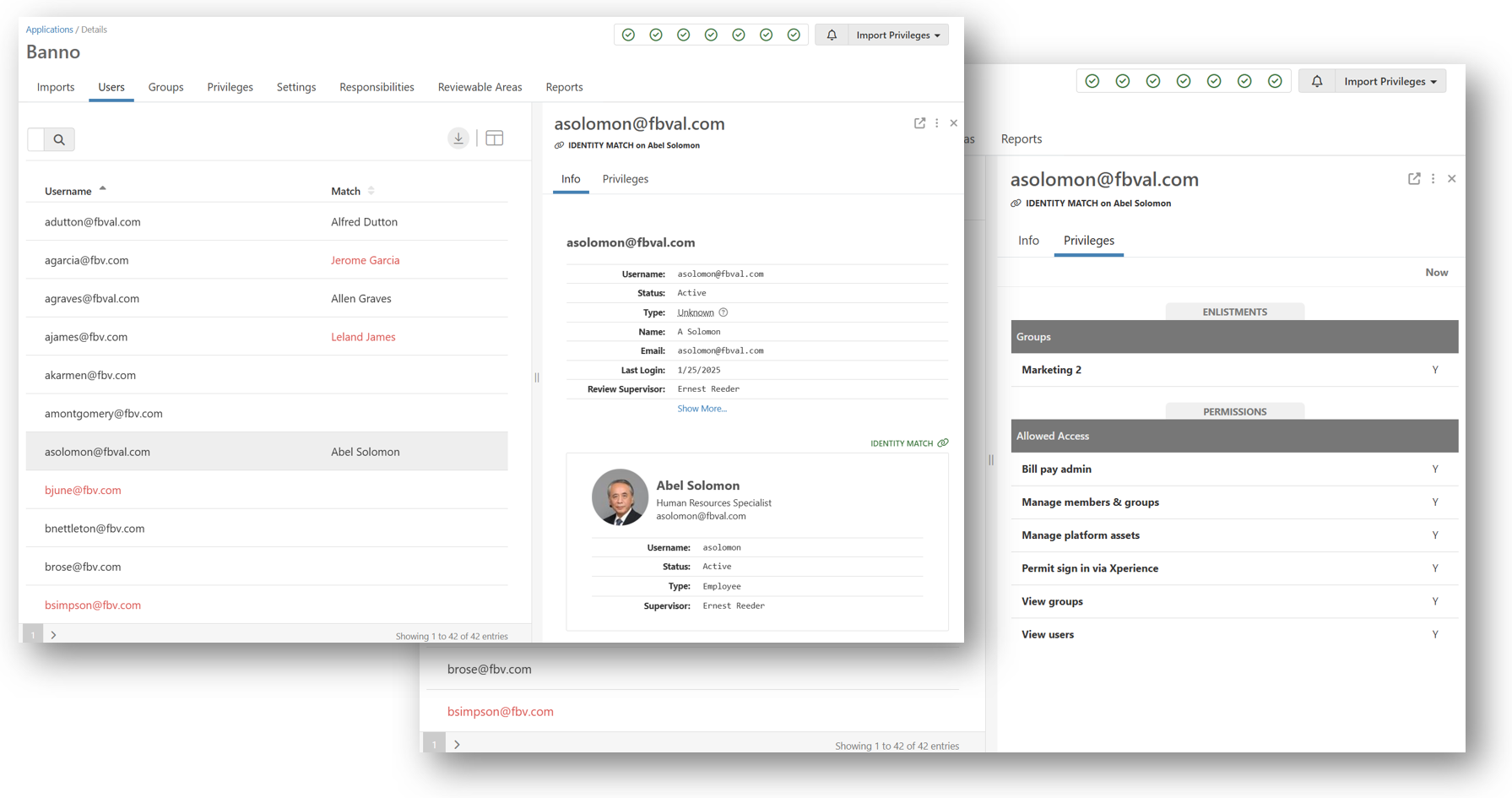
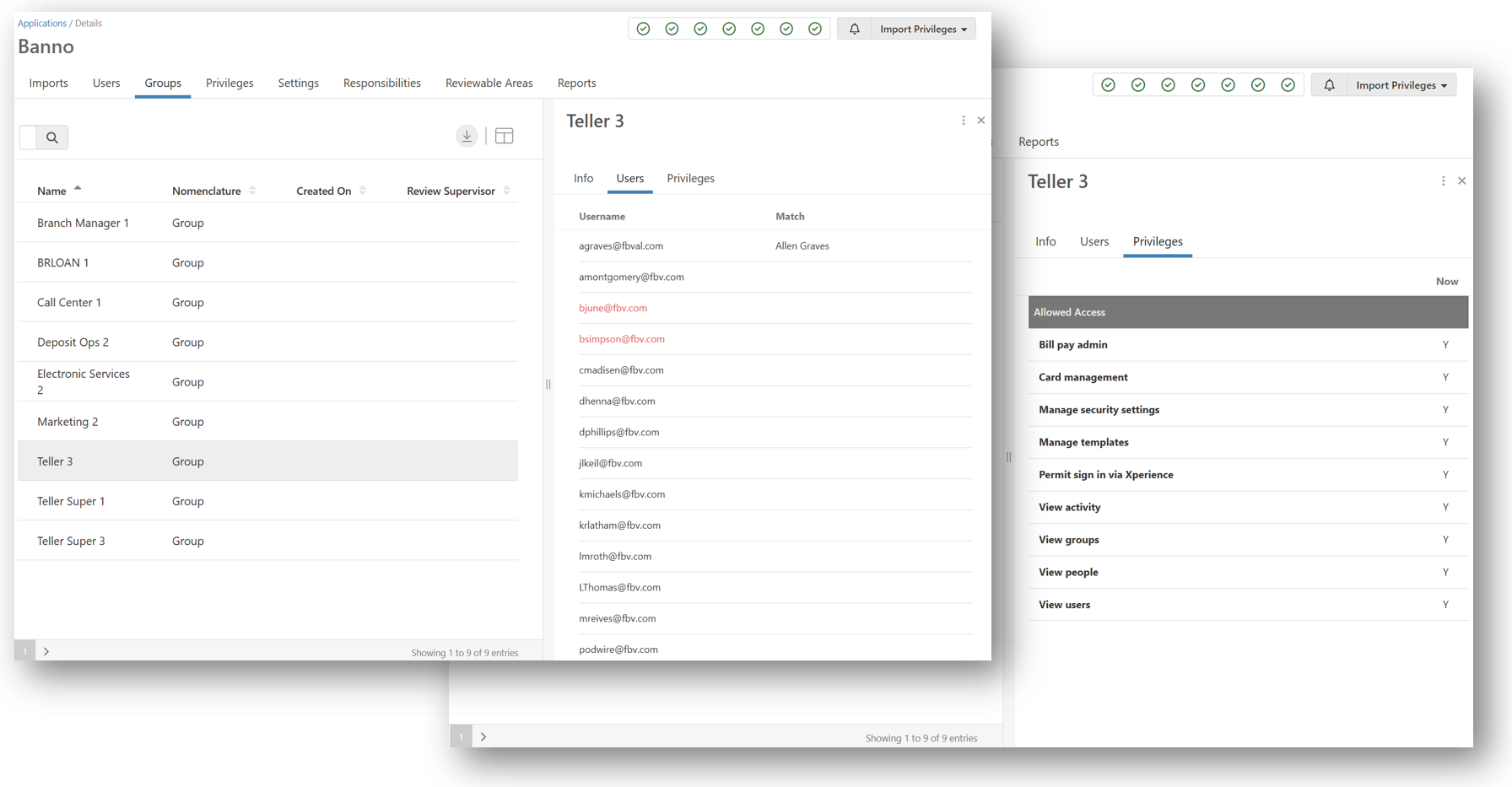
User and Group Privileges
The Users and Groups tabs on the application are the ultimate place for application managers to review their imported and formatted permission data prior to starting a review.
Within the Users area, you can view the user counts, browse through a list of users of the application, view a test identity match for each user, and drill down into the exact privilege data that will be leveraged during the next review.
Within the Groups area, you can view the group counts, browse through a list of users assigned to the group, and drill down into the exact privilege data that will be leveraged during the next review.
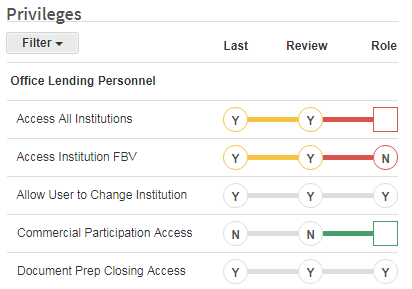
Then vs. Now - Permission Dumbbells
The "permission dumbbells" help streamline the review process by offering visual information of essential data so that permissions in the previous review can be compared to those in the current view. If the application also considers the role of each user, the Role column identifies whether the permission is set to the level or value expected for that role. When coupled with a multi-user review, the opportunity for many people of various levels to sign-off on permission integrity exists.
Permission Usage
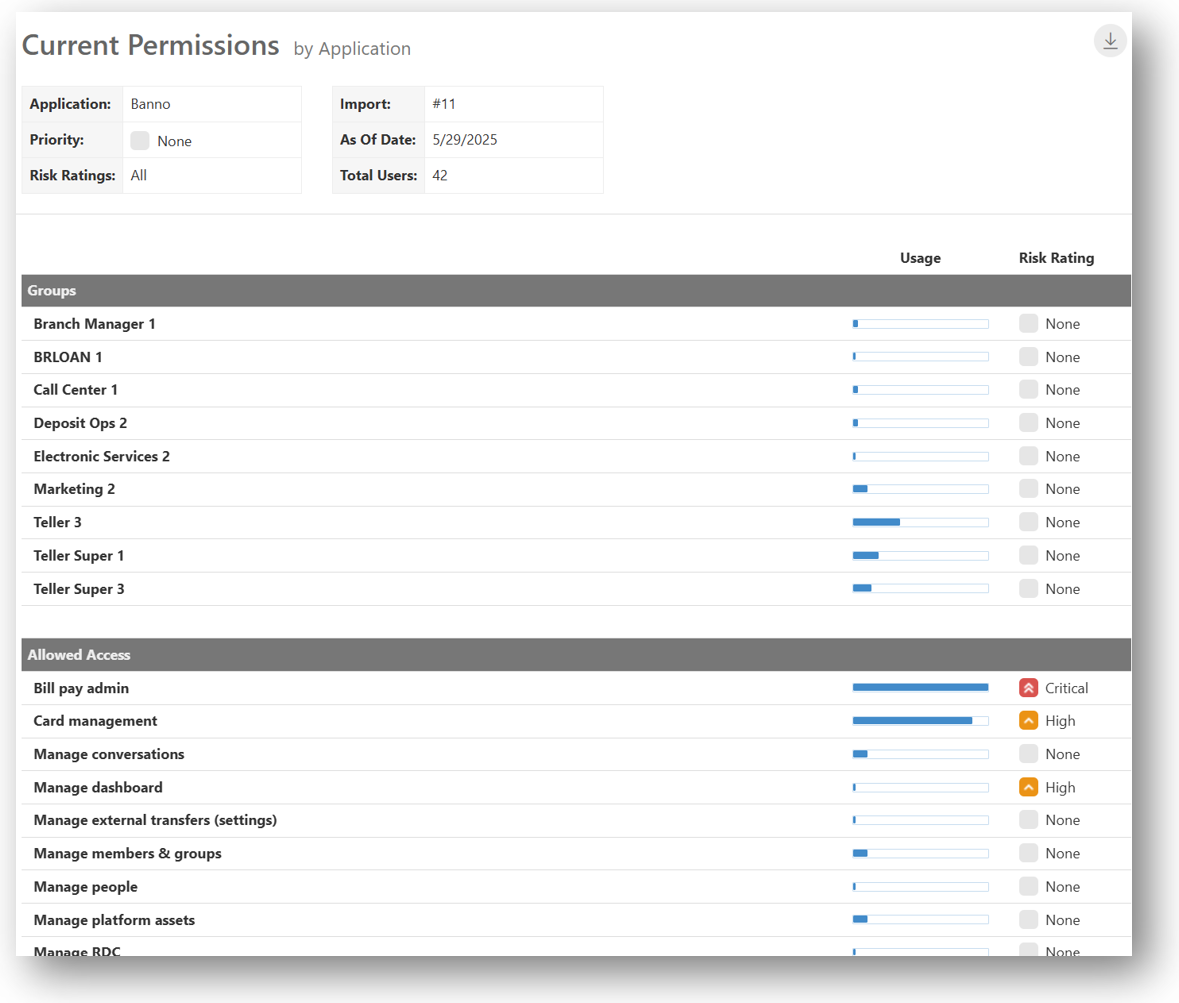
Enhanced reporting allows you to visualize the usage (across all users) for all privileges within an application, which helps to identify overly loose provisioning.